- Enormous trove of 149 million credentials exposed online
- Included usernames and passwords for banking, social media, and .gov accounts
- It isn't known how long the database was exposed for, but it has now been taken down
Cybersecurity researcher Jeremiah Fowler (via ExpressVPN) has once again uncovered a huge publicly accessible trove of data.
The massive container of unique usernames and passwords was exposed on the web without any password or encryption protection.
The data contained over 149 million combinations of usernames and passwords totalling around 98 gigabytes of credentials spanning online accounts of almost every kind.
149,000,000 credentials exposed
The credentials found within the container covered financial services including cryptocurrency wallets, trading accounts, and banking account details. Social media and dating app credentials were also included in the database.
Outside of personal accounts, a number of email accounts using the .gov domain were found within the container.
Very little is known about the origin of the exposed cloud storage container, but Fowler notes that traces of infostealer and keylogging malware was present in the database. Upon discovery, Fowler attempted to trace the owners of the account, but was unable to find any associated information.
Instead, Fowler attempted to contact the hosting provider who said that the container was being hosted by a subsidiary operating independently. It took almost one month to have the container taken down, Fowler notes.
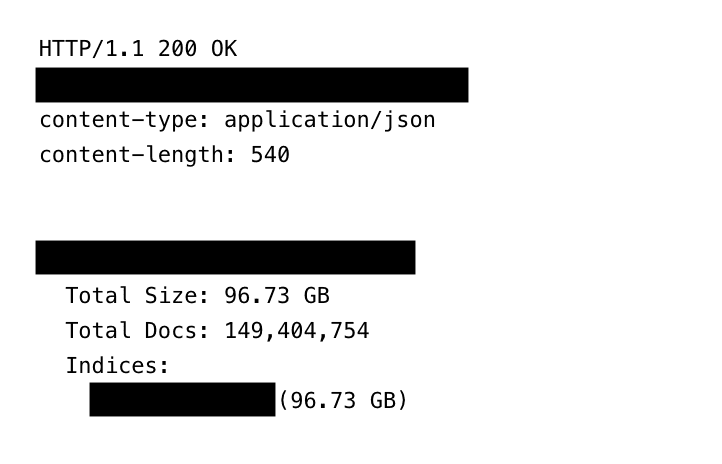
Interestingly, the credentials stored within the database were indexed in such a way as to make them easily searchable using the “host_reversed path”, meaning that the database could have been the work of an organized hacker, or may have been a research database.
A database of this size and scope could be used for highly nefarious purposes, such as spear-phishing, banking and credit fraud, and even identity theft. It is not currently known how long the database was left exposed.
The best password managers are one of the top ways to keep your credentials safe from being stolen. Many password managers store your usernames and passwords in an encrypted vault using two-factor authentication, and will scour the dark web to check if any of your credentials have been exposed.
Source: TechRadar